Rent a furnished apartment like you would book a hotel room for short-term rentals or extended stays. We offer flexible living with no long-term commitment in a stylish home.

Lodgeur® is for traveling professionals and digital nomads who want to stay in a beautiful property. Short-term rentals or extended stays. A place that feels like a home-away-from-home. Whether it’s for a few nights, weeks, or months.
The comfort and consistency of a hotel. But without the hassle of a check-in desk and drab decor. Our guests want beautifully-designed homes. But without invasive and amateur hosts.

Move-in ready homes. A space to work, cook, and relax. Whether traveling solo, as a couple, family, or with colleagues. One or two bedrooms, a kitchen, a living room, and a desk.
Relax, we take care of it. Everything’s included and set up for you already: utilities, fast WiFi internet, and complimentary biweekly housekeeping on extended stays.
On-demand living. Book for any length of stay: a weekend, a week, or a few months. And if you don’t know how long you need, you can move out with just 14 days’ notice.
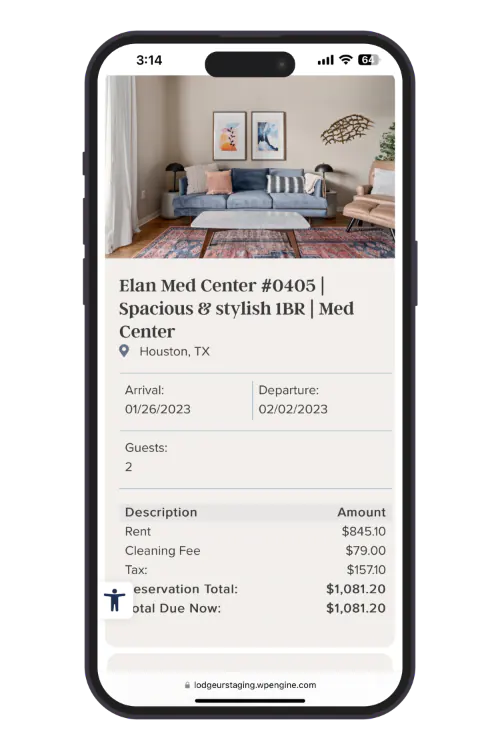
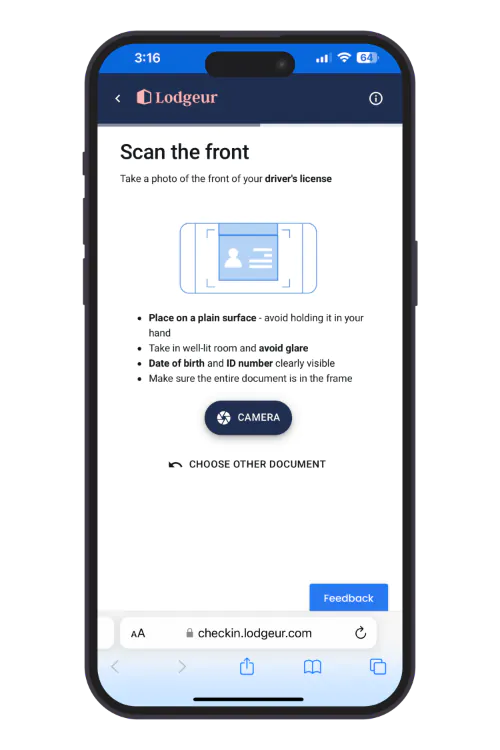
Rent a furnished apartment in three easy steps. From the comfort of your sofa to ours. No need to call for a quote or visit us during business hours, you can book online 24/7/365. No lengthy application forms, no credit check. Once you’ve made your reservation, you will receive a link to complete our online check-in with your ID through our secure guest verification portal.
We’re professional hosts, dedicated to designing furnished apartments in Houston that are stylish, comfortable and available on-demand. This is not our first rodeo: learn more about our story and team.
Featured in
Guests Hosted

1,500+ Reviews
We’ve hosted thousands of guests. Business and leisure travelers, executives and interns, travel nurses and doctors, people visiting friends and family, temporary relocations for housing repairs and renovations, actors and sportspeople, concertgoers and sports fans, etc…

From startups to large organizations, we provide relocation housing for engineers, professional athletes, and executives on assignment.

Healthcare travelers enjoy our stylish and flexible apartments, with easy access to hospitals and medical schools.

Recommended by Joe’s House. From the first consultation to extended treatment periods, we host patients visiting the Texas Medical Center hospitals.

Remote workers can book our signature Digital Nomad Suites with an office, monitor, whiteboard, and more. WFH and then explore Houston.

No need to sleep on an airbed or buy furniture for the summer. Take care of yourself and make a strong impression.

Whether you’re in town for a seminar or semester, we’re close to campus (University of Houston, Rice, and more).

We select properties in the best areas of Houston. Apartments that are close to your office, attractions and places to eat and drink. Our interior designers craft the decor of each property one-by-one. The result is a place that feels like a home-away-from-home. We have high quality standards. This means we offer the comfort and consistency of a hotel. Things like the same comfortable bed and bedding. A desk to work and fast internet. And fully equipped kitchens.
Take a virtual tour:
Mid Main Lofts
Elan Med Center

Guests love this trendy 2016 loft-style complex most for its location in Houston’s most walkable neighborhood, Midtown. With endless choices for food and drink and its own station on the METRORail, Mid Main Lofts is the perfect home base to enjoy Houston.

Situated in the heart of the TMC, Elan Med Center is popular with guests seeking treatment or working at MD Anderson, Memorial Hermann, Methodist Hospital, and Texas Children’s Hospital. This 2013 mid-rise complex sits between MD Anderson and the VA Hospital.
Lodgeur’s Class-A apartment buildings offer convenience and modern luxuries. Our apartment communities were handpicked for extended-stay and short-term travelers, blending hotel-quality amenities with apartment-style convenience.

Save on parking costs with complimentary parking in the gated parking garage attached to the apartment building.

Stay active with 24/7 access to an on-site fitness center stocked with professional-grade cardio and strength equipment.

Kick back by the pool, soaking up the Texas sun. Fire up the poolside gas grills for a quick barbecue.

Work from the on-site lounges when you need a change of scenery. Sofas, tables, and desks make it easy to WFH.

No need to arrange pickup up and dropping off keys with a host. Our smart tech offers a socially distanced self-check-in at any time.

Our interior designers craft the decor of each property one-by-one.

Fully-equipped kitchens, whether you’re cooking or ordering take-out. Because eating out every meal is tiring and expensive.

Fast WiFi internet, a desk, and office chair. For a work-friendly stay. Whether you’re working hard or just catching up on social media.

Get a great night’s sleep on our memory foam mattresses.You’ll be ready explore the city or to conquer the world.

Bathrooms with plenty of storage, MALIN+GOETZ toiletries, and two sets of plush towels per person.

We’re pros, neat and tidy. We rent our properties out all year. You won’t have to deal with a host’s stuff all over the place.

We’ll give you your privacy during your stay. Text, email or call if you need anything.
Yes! Lodgeur offers both short-term and extended stay rentals. You can stay as little as two nights and as long as you want (our longest stay to date was 13 months).
Furnished apartments are typically more expensive to rent than unfurnished apartments because they are ready to move in and do not require any additional cost for furniture or decor. Furnished apartments also include extra amenities and services in the rent, such internet access, smart TVs, housekeeping, and utilities. The cost of a furnished apartment varies depending on the size, location, and amenities included. Generally, furnished apartments cost more each month, but they may be more cost-effective if you need flexible temporary housing. Lodgeur's flexible furnished apartments don't require a long-term commitment: on extended stays, you can move out penalty-free with just 14 days notice.
Lodgeur's rates depend on when you're staying with, how long your stay is, and which unit you choose. Guests who book 27-night stays often find that it's cheaper to stay for 30 nights (no taxes on stays over 30 nights). Note that you will incur a one-time cleaning charge on stays under 30 nights, which means that the average cost per night of a 10-night stay is less than a 2-night stay. Read more about Lodgeur's cleaning fees on furnished apartments here.
A Lodgeur furnished apartment includes everything you need for both short and extended stays. The apartment is extensively furnished and tastefully decorated. The bedrooms typically include a king-size bed with a 12-inch memory foam mattress, four pillows, and a full set of linens. In the bathroom, you'll have two sets of towels per person, toiletries, a hair dryer, and even a flat iron. The kitchen is fully-equipped, with extras that include a blender, slow cooker, rice cooker, toaster, electric kettle, coffee machine, and tri-ply steel cookware. There's also a dishwasher, washer, and dryer to make life easier. And for your entertainment, each living room and bedroom comes equipped with a smart TV to stream your favorite content. There's also a bluetooth speaker, fast WiFi internet, and desk if you need to work. We even include housekeeping every two weeks on extended stays.
Airbnb doesn't have apartments. It's a booking platform that charges guests a percentage fee to book a short-term stay or an extended stay. We’re a top-rated short-term rental brand in Houston. We rent our properties out all year. We're pros, neat and tidy. That means a clutter-free rental. You won’t have to deal with a host's stuff all over the place. You can book a Lodgeur furnished apartment on Airbnb or directly on Lodgeur's website. See our blog post about saving money on your next rental.
Lodgeur's listings are furnished apartments in Class-A apartment communities, available on flexible terms. Unlike a hotel, with Lodgeur each unit includes a fully-equipped kitchen, washer and dryer, along with the other amenities you would expect from an apartment over a hotel room. We do not offer daily cleaning service, room service, or a front desk which helps to reduce the cost of renting. But we do offer 24/7 self-check-in and support by text, phone, and email.